Beachte: Update des Beitrags!
Nach den Anpassungen der Apache Configuration in Folge des Poodle Bugs erhielt ich zu Beginn der Woche eine Rückmeldung einer Vista Nutzerin aus dem Kollegium, dass sie nicht mehr auf unsere Seiten zugreifen könne. Ich nahm das zuerst nicht weiter ernst, tippte auf lokale Probleme. Dann stellte ich unter Cubian X fest, dass Chromium nur noch einen 113er Fehler anzeigte, der für
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
steht und Iceweasel merkte an
ssl_error_no_cypher_overlap
Diverse Browser unter Android 4.0.3 (Lightning, Tint Browser, Zirco) wollten ebenfalls nicht mehr meine eigenen HTTPS verschlüsselten Seiten aufrufen. Während unter Android der Firefox noch einsetzbar war, so ging auf meinem Spielkistchen mit Cubian X gar nichts mehr. Die Software auf diesem System lässt sich nicht einfach aktualisieren – meine Apache-Konfiguration war für das Ding schlicht „zu sicher“.
Ich kam dann irgendwann auf Idee, die unterstützten Cipher Suiten miteinander zu vergleichen. Das geht direkt bei Qualys SSL Labs – oder für den Browser auch hier: https://cc.dcsec.uni-hannover.de/check . Die Schuppen fielen dann endlich von den Augen.
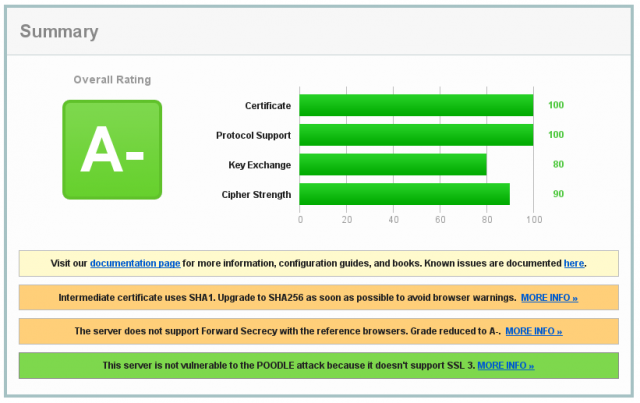
Sichere Konfiguration
Eintrag:
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ALL:!ADH:RC4+RSA:+HIGH:+MEDIUM:!LOW:!SSLv2:!SSLv3:!EXPORT
Ergebnis unter Debian:
Unterstützte Browsersuiten:
| Handshake Simulation | |||
| Android 2.3.7 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| Android 4.0.4 | Protocol or cipher suite mismatch | Fail3 | |
| Android 4.1.1 | Protocol or cipher suite mismatch | Fail3 | |
| Android 4.2.2 | Protocol or cipher suite mismatch | Fail3 | |
| Android 4.3 | Protocol or cipher suite mismatch | Fail3 | |
| Android 4.4.2 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| BingBot Dec 2013 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| BingPreview Jun 2014 | Protocol or cipher suite mismatch | Fail3 | |
| Chrome 37 / OS X R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) FS |
128 |
| Firefox 24.2.0 ESR / Win 7 | Protocol or cipher suite mismatch | Fail3 | |
| Firefox 32 / OS X R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) FS |
128 |
| Googlebot Jun 2014 | Protocol or cipher suite mismatch | Fail3 | |
| IE 6 / XP No FS 1 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| IE 7 / Vista | Protocol or cipher suite mismatch | Fail3 | |
| IE 8 / XP No FS 1 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| IE 8-10 / Win 7 R | Protocol or cipher suite mismatch | Fail3 | |
| IE 11 / Win 7 R | TLS 1.2 | TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) No FS |
128 |
| IE 11 / Win 8.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| IE Mobile 10 / Win Phone 8.0 | Protocol or cipher suite mismatch | Fail3 | |
| IE Mobile 11 / Win Phone 8.1 | TLS 1.2 | TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) No FS |
128 |
| Java 6u45 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| Java 7u25 | Protocol or cipher suite mismatch | Fail3 | |
| Java 8b132 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) FS |
128 |
| OpenSSL 0.9.8y | Protocol or cipher suite mismatch | Fail3 | |
| OpenSSL 1.0.1h | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| Safari 5.1.9 / OS X 10.6.8 | Protocol or cipher suite mismatch | Fail3 | |
| Safari 6 / iOS 6.0.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 7 / iOS 7.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 8 / iOS 8.0 Beta R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 6.0.4 / OS X 10.8.4 R | Protocol or cipher suite mismatch | Fail3 | |
| Safari 7 / OS X 10.9 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Yahoo Slurp Jun 2014 No SNI 2 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| YandexBot Sep 2014 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| (1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it. | |||
| (2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI. | |||
| (3) Only first connection attempt simulated. Browsers tend to retry with a lower protocol version. | |||
| (R) Denotes a reference browser or client, with which we expect better effective security. | |||
| (All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE). | |||
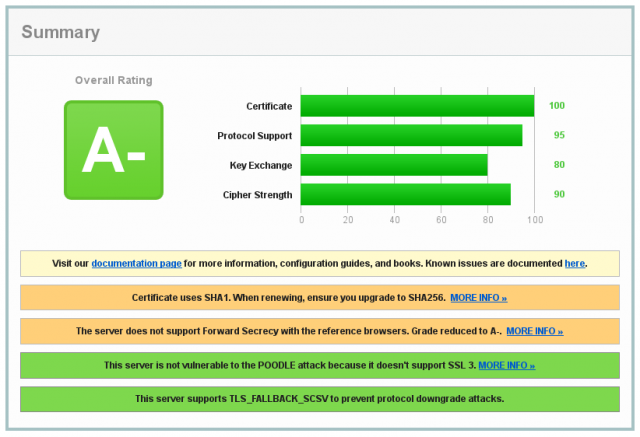
Überarbeitete Konfiguration
Eintrag:
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5
Ergebnis unter Debian:
Unterstützte Browsersuiten:
| Handshake Simulation | |||
| Android 2.3.7 No SNI 2 | TLS 1.0 | TLS_RSA_WITH_RC4_128_SHA (0x5) No FS RC4 |
128 |
| Android 4.0.4 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Android 4.1.1 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Android 4.2.2 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Android 4.3 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Android 4.4.2 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| BingBot Dec 2013 No SNI 2 | TLS 1.0 | TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) No FS |
128 |
| BingPreview Jun 2014 | TLS 1.0 | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) FS |
256 |
| Chrome 37 / OS X R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) FS |
128 |
| Firefox 24.2.0 ESR / Win 7 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Firefox 32 / OS X R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) FS |
128 |
| Googlebot Jun 2014 | TLS 1.0 | TLS_ECDHE_RSA_WITH_RC4_128_SHA (0xc011) FS RC4 |
128 |
| IE 6 / XP No FS 1 No SNI 2 | Protocol or cipher suite mismatch | Fail3 | |
| IE 7 / Vista | TLS 1.0 | TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) No FS |
128 |
| IE 8 / XP No FS 1 No SNI 2 | TLS 1.0 | TLS_RSA_WITH_RC4_128_SHA (0x5) No FS RC4 |
128 |
| IE 8-10 / Win 7 R | TLS 1.0 | TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) No FS |
128 |
| IE 11 / Win 7 R | TLS 1.2 | TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) No FS |
128 |
| IE 11 / Win 8.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| IE Mobile 10 / Win Phone 8.0 | TLS 1.0 | TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) No FS |
128 |
| IE Mobile 11 / Win Phone 8.1 | TLS 1.2 | TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) No FS |
128 |
| Java 6u45 No SNI 2 | TLS 1.0 | TLS_RSA_WITH_RC4_128_SHA (0x5) No FS RC4 |
128 |
| Java 7u25 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) FS |
128 |
| Java 8b132 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) FS |
128 |
| OpenSSL 0.9.8y | TLS 1.0 | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39) FS |
256 |
| OpenSSL 1.0.1h | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| Safari 5.1.9 / OS X 10.6.8 | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) FS |
128 |
| Safari 6 / iOS 6.0.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 7 / iOS 7.1 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 8 / iOS 8.0 Beta R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Safari 6.0.4 / OS X 10.8.4 R | TLS 1.0 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) FS |
256 |
| Safari 7 / OS X 10.9 R | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) FS |
256 |
| Yahoo Slurp Jun 2014 No SNI 2 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| YandexBot Sep 2014 | TLS 1.2 | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) FS |
256 |
| (1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it. | |||
| (2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI. | |||
| (3) Only first connection attempt simulated. Browsers tend to retry with a lower protocol version. | |||
| (R) Denotes a reference browser or client, with which we expect better effective security. | |||
| (All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE). | |||

Hallo,
ich hatte das gleiche Problem, allerdings lag es bei mir daran das ich TLS 1.0 exkludiert hab:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1
Und anscheinend kann der googlebot (https://www.ssllabs.com/ssltest/viewClient.html?name=Googlebot&version=Jun%202014) (sowie eine reihe anderer Crawler) nur über TLS 1.0 eine Verbindung herstellen.
Bei mir hat also gereicht einfach TLSv1 zuzulassen.
Hier befindet sich inzwischen ein Update für den obigen Beitrag, der auch die intermediären Zertifikate beachtet.